systemd&&docker镜像支持systemd
k8s环境中,经常需要一个容器进行一些调试,特意打包了常用小工具
Dockerfile
FROM harbor.iovhm.com/hub/centos:7
RUN curl -o /etc/yum.repos.d/CentOS-Base.repo https://mirrors.aliyun.com/repo/Centos-7.repo && \
sed -i -e '/mirrors.cloud.aliyuncs.com/d' -e '/mirrors.aliyuncs.com/d' /etc/yum.repos.d/CentOS-Base.repo && \
curl -o /etc/yum.repos.d/epel.repo https://mirrors.aliyun.com/repo/epel-7.repo && \
yum makecache && \
yum install -y which wget openvpn telnet && \
yum clean all && \
curl -o /usr/bin/systemctl https://raw.githubusercontent.com/gdraheim/docker-systemctl-replacement/master/files/docker/systemctl.py && \
chmod +x /usr/bin/systemctl && \
true
COPY ./entrypoint.sh /root/entrypoint.sh
RUN chmod +x /root/entrypoint.sh
CMD [ "/root/entrypoint.sh" ]
WORKDIR /root
entrypoint.sh
#!/bin/bash
set -x
echo "busybox ..."
# 判断环境变量 OPENVPN 是否存在并且值为 1,决定是否开启 OpenVPN 客户端
if [ "${OPENVPN}" == "1" ]; then
echo "start openvpn-client ..."
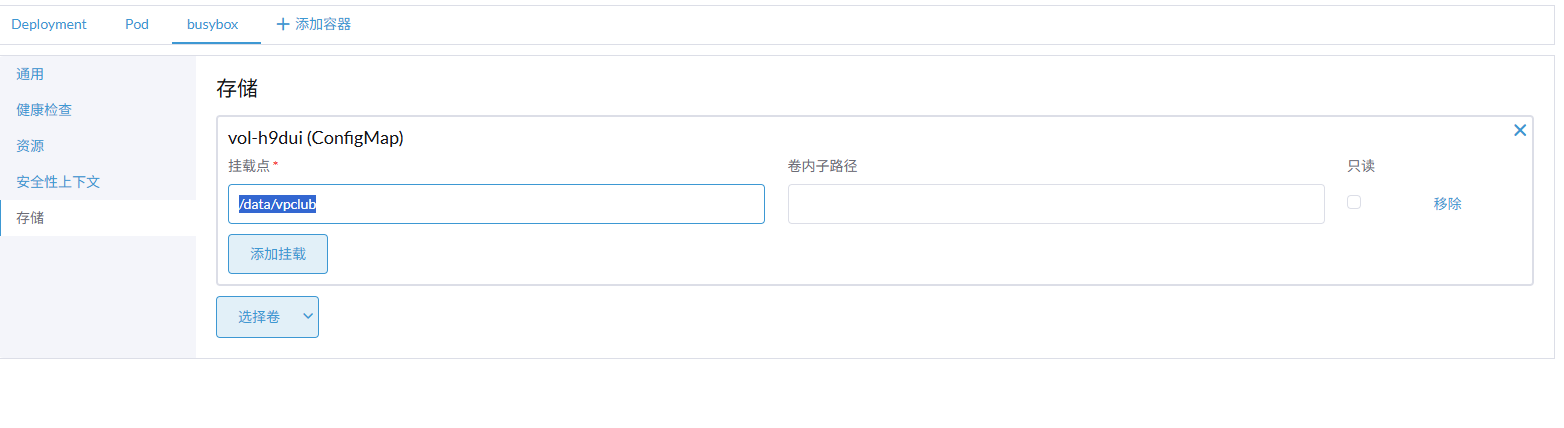
/usr/sbin/openvpn --config /data/vpclub/ovpn_configuration_file.ovpn &
# 等待 OpenVPN 启动
sleep 10
else
echo "OPENVPN environment variable not set or not equal to 1. Skipping OpenVPN client setup."
fi
# 判断环境变量 IP_FORWARD 是否存在且值为 1,决定是否开启 IP 转发
if [ "${IP_FORWARD}" == "1" ]; then
echo "Enabling IP forwarding..."
echo 1 >/proc/sys/net/ipv4/ip_forward
echo "start ip_forward ..."
# 从文件读取 IP_FORWARD_RULES
if [ -f "/data/vpclub/IP_FORWARD_RULES.txt" ]; then
IP_FORWARD_RULES=$(cat /data/vpclub/IP_FORWARD_RULES.txt)
else
echo "IP_FORWARD_RULES file not found. Skipping batch IP forwarding setup."
continue
fi
# 批量设置 IP 转发规则
if [ -n "${IP_FORWARD_RULES}" ]; then
IFS=$'\n' read -r -d '' -a rules <<<"${IP_FORWARD_RULES}"
for rule in "${rules[@]}"; do
# 修改解析逻辑,支持新的格式
IFS=',' read -r SRC_IP_PORT DEST_IP_PORT DEST_PROTO <<<"$rule"
IFS=':' read -r SRC_IP SRC_PORT <<<"$SRC_IP_PORT"
IFS=':' read -r DEST_IP DEST_PORT <<<"$DEST_IP_PORT"
DEST_PROTO=${DEST_PROTO:-tcp} # 默认协议为tcp
# 添加PREROUTING规则
iptables -t nat -I PREROUTING ! -s ${DEST_IP}/32 -p ${DEST_PROTO} --dport ${SRC_PORT} -j DNAT --to ${DEST_IP}:${DEST_PORT}
# 添加POSTROUTING规则
iptables -t nat -I POSTROUTING -d ${DEST_IP}/32 -p ${DEST_PROTO} -j MASQUERADE
done
else
echo "No IP_FORWARD_RULES provided. Skipping batch IP forwarding setup."
fi
else
echo "IP_FORWARD environment variable not set or not equal to 1. Skipping IP forwarding setup."
fi
echo "success ..."
tail -f /dev/null
隐藏秘籍,内置了openvpn-client
version: "3"
services:
busybox:
image: harbor.iovhm.com/public/busybox:latest
container_name: busybox
network_mode: host # 注意一定要是host模式,因为他默认监听在容器内,并不能与主机直接通讯
privileged: true
restart: always
volumes:
- ./ovpn_configuration_file.ovpn:/data/vpclub/openvpn/ovpn_configuration_file.ovpn
command: "/usr/sbin/openvpn --config /data/vpclub/openvpn/ovpn_configuration_file.ovpn"
链接到集群内
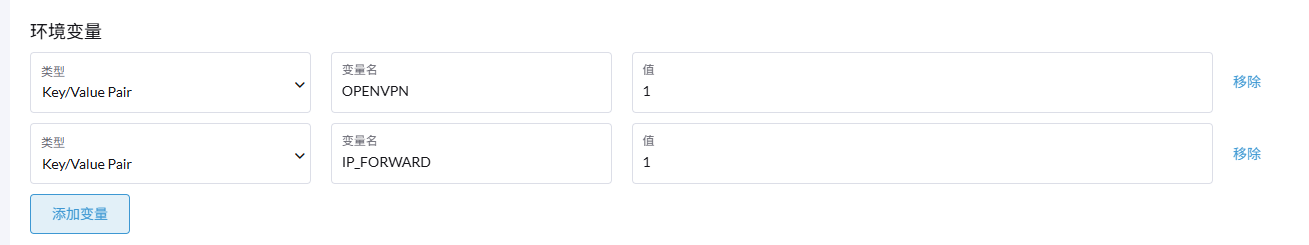
增加两个环境变量
- 开启内置的VPN: OPENVPN=1
- 开启端口转发:IP_FORWARD=1
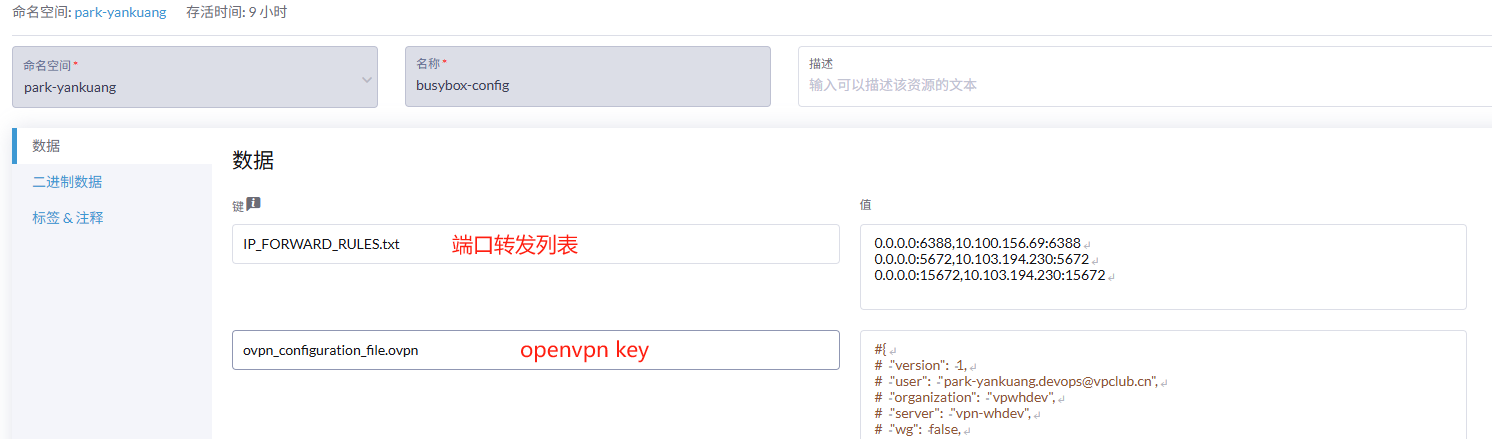
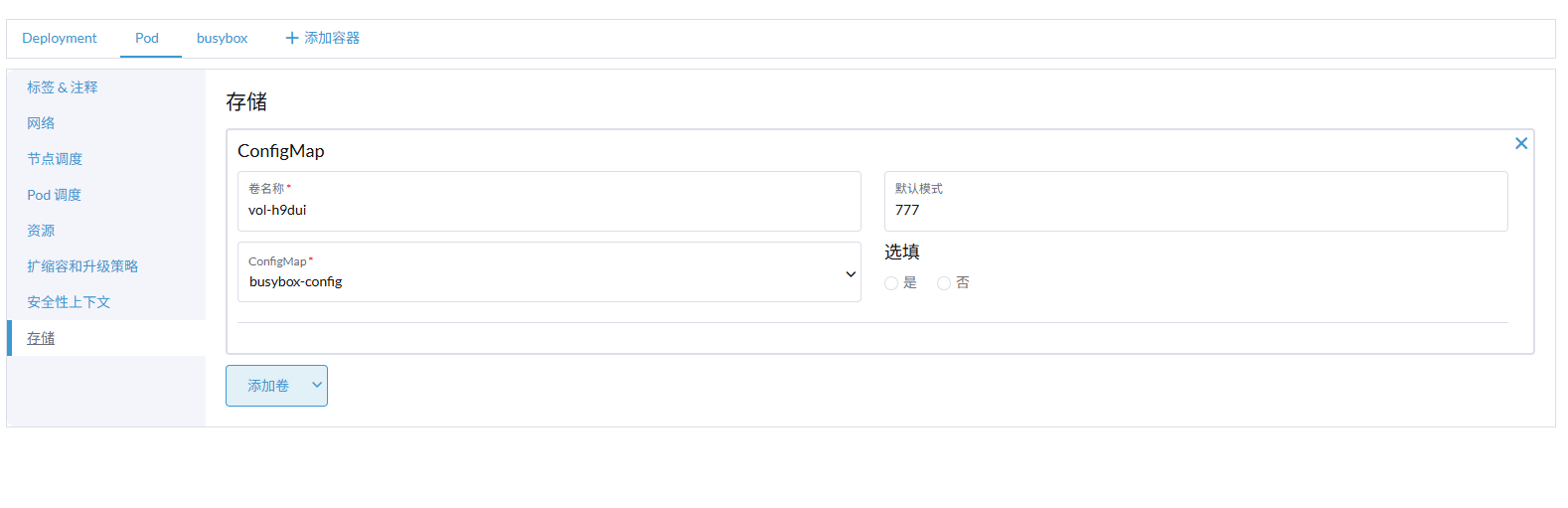
编写configmap
重要:如下两个配置的名称要对应上,因为启动脚本里面写死了
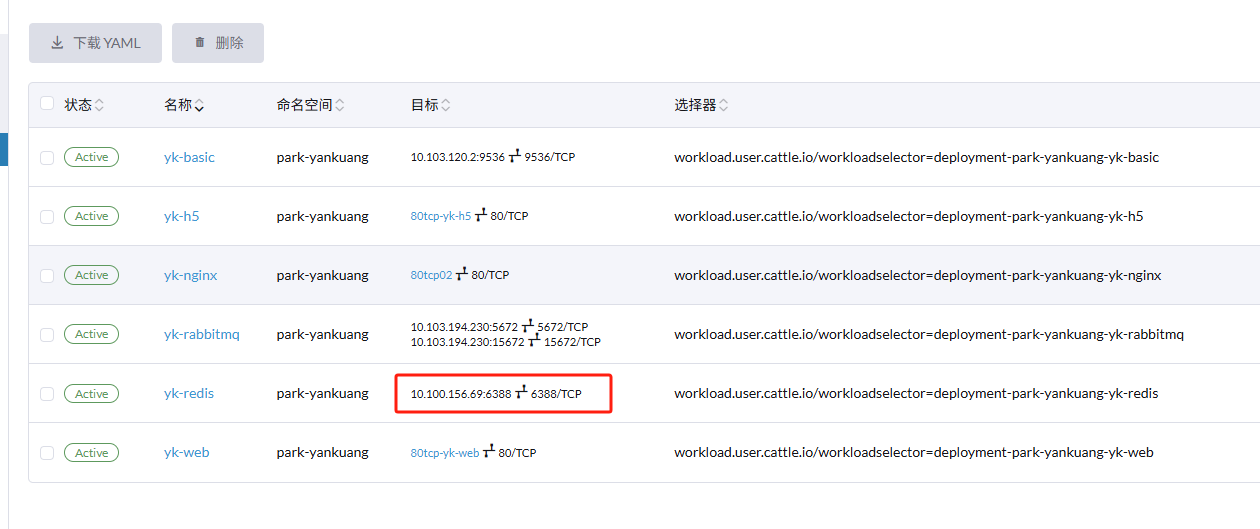
- 端口转发规则 IP_FORWARD_RULES.txt
格式为:SRC_IP:SRC_PORT,DST_IP:DST_PORT,一行一个,
0.0.0.0:6388,10.100.156.69:6379
0.0.0.0:5672,10.103.194.230:5672
0.0.0.0:15672,10.103.194.230:15672
其中的IP为服务发现的IP
- VPN客户端秘钥文件:ovpn_configuration_file.ovpn
可以到pritunl中下载后用记事本打开后粘贴进去